Welcome to the Cortado Blog
The Cortado Blog is your guide on company-managed smartphones and tablets. Here you will find MDM insights, best practices as well as tips and tricks for the effective and secure use of smartphones and tablets in your organization.
-

iOS Business Container: Securely Separating Corporate Data on iPhone
How organizations separate personal and corporate iPhone use: implement an iOS business container with MDM—securely, practically, and GDPR-compliant.
-

Mobile Device Management for Hybrid Work Models: Benefits & Best Practices
A practical guide to Mobile Device Management in hybrid work environments. Security, compliance, and best practices for IT decision-makers.
-

IT Plan 2026: Why a Mobile Device Status Check Belongs on Every IT Agenda
Mobile devices are business-critical. A structured status check creates transparency for IT planning, budgeting, and priority setting for 2026.
-

How to Create a Mobile Security Policy: The Ultimate Guide for Enterprises
A practical guide to creating a mobile security policy for enterprises. Covers BYOD, GDPR, MDM, and best practices for secure mobile work.
-

Apple MDM Migration: Why Now Is the Perfect Time to Switch to Cortado
No More Complex MDM Transitions: Apple Enables Migration to cortado MDM Without Resetting Devices – Secure, Fast, and Without Data Loss.
-

Mac Management: The Ultimate Guide for IT Administrators
The management of Mac devices has become a strategic IT priority. Discover how modern MDM tools, automation and Apple services make device management more efficient and secure than ever – from deployment right through to decommissioning. The management of Mac devices in corporations has evolved in recent years from a niche task to a strategic…
-

Enterprise MDM Security: Best Practices for Securing Large Device Fleets
Discover the five key security areas for protecting large mobile device fleets – including practical tips for maximum security and compliance.
-
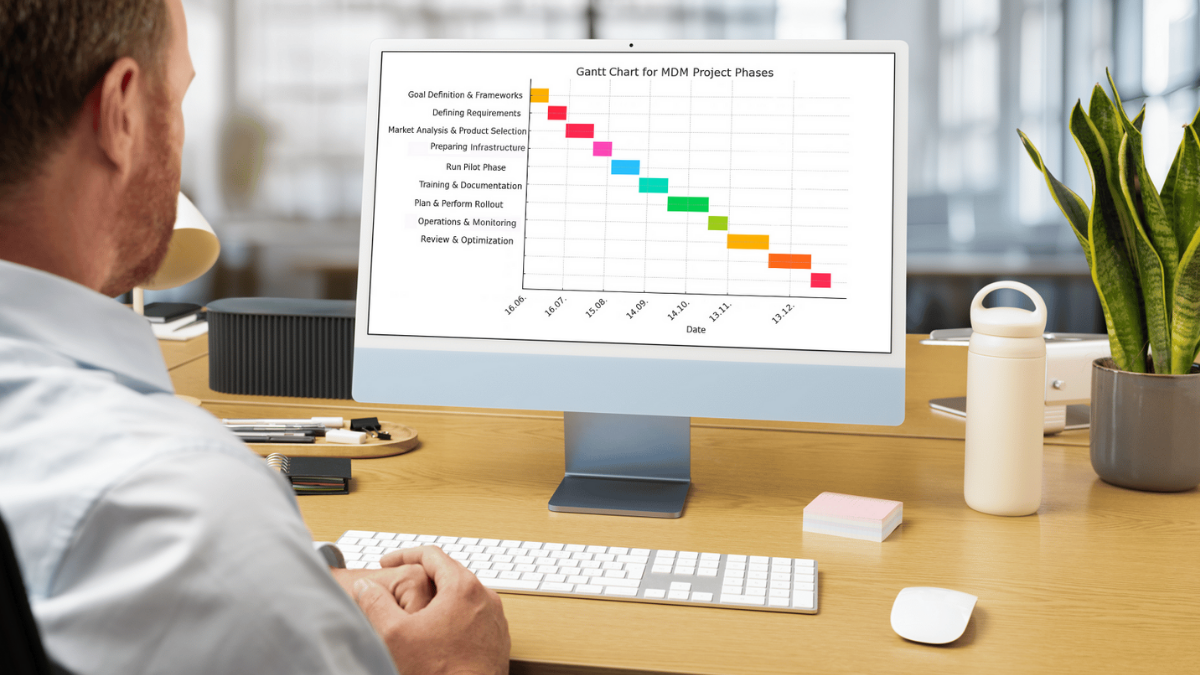
The 11-Step Plan for Successful MDM Rollouts in Large Enterprises
Our 11-step plan gives you the essential know-how to successfully roll out Mobile Device Management in large enterprise environments – including a hands-on guide available for download.
-

Enterprise MDM: The biggest challenges of managing large device fleets – and how Cortado solves them
When a company isn’t just managing a few hundred but thousands or even tens of thousands of smartphones and tablets, mobile device management becomes a serious discipline.
-

WWDC 2025: Apple Takes Device Management to the Next Level
Apple unveils major Mobile Device Management updates at WWDC 2025. Get the full overview now.
-
Apple Intelligence on Company iPhones: Productivity Booster or Privacy Concern?
Apple Intelligence promises productivity gains for businesses — but what about data privacy and security? Explore the key opportunities and challenges now!